1. Understanding Different Types of Malware
Let’s dive into the most common types of malware, their characteristics, and how they can affect your computer or network.
1.1. Computer Viruses
A computer virus is a malicious program that self-replicates by modifying other computer programs and inserting its own code. Viruses often spread through social engineering tactics, such as phishing, and exploit vulnerabilities in software to infect systems. They can cause system failure, corrupt or modify files, and even steal sensitive data.
1.2. Computer Worms
Worms are self-replicating malware programs that can spread without human interaction or host dependency. They often use computer networks and software vulnerabilities to infect and cause damage to multiple devices simultaneously. Worms can delete or modify files, steal data, install backdoors for hackers, and launch Distributed Denial of Service (DDoS) attacks.
1.3. Trojan Horses
Trojans are deceitful malware programs that disguise themselves as legitimate software or files. Once installed, they can execute harmful actions, such as stealing data, spying on users, and granting unauthorized access to a computer or network. Trojans often spread through phishing emails, malicious downloads, or direct messages.

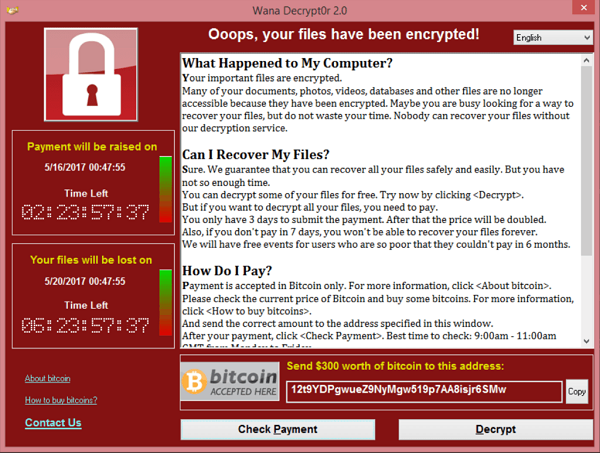
1.4. Ransomware
Ransomware is a type of malicious software that can take control of a user’s device and encrypt their stored data, holding it hostage until a ransom is paid. The criminals behind ransomware attacks often demand payment in bitcoin to keep their identities concealed. In addition to this, they may resort to blackmailing the victim by threatening to report them for possessing pirated material or illegal pornography, or by threatening to expose private information or images.
It can spread through phishing emails, malvertising, and exploiting vulnerabilities in software. Ransomware attacks can result in downtime, data leaks, and financial loss.
Having secure and reliable backups stored in a separate environment of your system is a crucial defence against ransomware attacks. Unfortunately, paying the ransom doesn’t always guarantee the return of your files, and attackers may even demand more money. Although not common, decryption tools have been successful against ransomware in the past. However, the most effective way to safeguard against Ransomware attacks is to take preventative measures, such as employing anti-malware tools and running regular scans.
1.5. Bots and Botnets
A bot is a system or device infected with malware that is remotely controlled. Botnets are a group of Bots used for coordinated attacks. Bots can be used to launch cyberattacks, compromise networks, steal information, relay spam, perform DDoS attacks, spread ransomware, and for keylogging.
Bots are easily available, and cybercriminals can even rent an army of bots from a dark web ‘business’ to execute their shady online activities.
1.6. Adware
Adware is a form of grayware that displays unwanted advertisements on a user’s device. It is often bundled with free software or disguised as legitimate applications. While adware might not be as harmful as other types of malware, it can still invade user privacy, share data with third parties, and lead to more severe malware infections.
1.7. Spyware
Spyware is a stealthy type of malware that infiltrates a device to monitor user activity, steal sensitive information, or perform other malicious actions. It can be challenging to detect and may lead to identity theft, financial fraud, or other privacy breaches.
1.8. Rootkits
Rootkits are malware programs that grant attackers remote control over a victim’s device, often without their knowledge. They are designed to let attackers in through a backdoor, allowing them to hijack or subvert security software, making it difficult, if not impossible, to detect and remove. A device infected with a Rootkit cannot be trusted, because a virus scan will show a false negative. The most common way to deal with Rootkits is a complete system rebuild or restoration from a good, trusted backup. Rootkits often spread through phishing and malicious downloads or attachments.
1.9. Fileless Malware
Fileless malware leverages built-in software, applications, and protocols in an operating system to execute malicious activities without the need for a file. It is memory-based and can piggyback on legitimate scripts, making it challenging to detect and remove.
1.10. Malvertising
Malvertising is a type of malware that spreads through infected ads on legitimate websites. It can lead to ransomware attacks, data theft, and financial fraud. Malvertising differs from adware, as adware is already present on a device, while malvertising comes from external sources.
2. How Malware Spreads
Malware can spread through various methods, such as exploiting software vulnerabilities, backdoors, social engineering, and blended threats. Below are six common ways malware spreads:
- Vulnerabilities: Security defects in software allow malware to exploit them and gain unauthorised access to the computer, hardware, or network.
- Backdoors: Intended or unintended openings in software, hardware, or networks that grant unauthorised access to attackers.
- Drive-by downloads: Unintended downloads of malware that occur when users visit infected websites or click on malicious links.
- Homogeneity: Increased risk of worm infections when all systems run the same operating system and are connected to the same network.
- Privilege escalation: Attackers gain escalated access to a computer or network and use it to mount further attacks.
- Blended threats: Malware attacks that combine characteristics from multiple types of malware, making them harder to detect and stop.
3. Detecting and Removing Malware
Detecting and removing malware can be challenging due to the increasing sophistication of attacks and the use of evasion techniques. Anti-malware software can help detect and remove malware, but prevention is always the best defense. Here are some best practices for detecting and removing malware:
- Use multi-factor authentication: Adding an extra layer of security to your accounts, such as two-factor authentication or biometric scans, can help prevent unauthorised access.
- Avoid suspicious emails, links, and websites: Be wary of attachments from unknown sources and do not click on suspicious links or visit untrusted websites.
- Adjust spam filters: Set your email spam filters to a high level to reduce the risk of receiving malicious emails.
- Keep software up to date: Regularly update your software to patch security vulnerabilities and protect against malware attacks.
- Know the warning signs of malware infection: Be aware of signs such as sluggish performance, freezing or crashing, unwanted pop-ups, or unauthorised emails sent from your account.
- Use antivirus software: Employ antivirus software to monitor and stop cyber threats, including malware.
- Back up files regularly: Regularly back up your data to ensure you can quickly recover from a malware infection.
4. Preventing Malware Infections
Preventing malware infections is crucial to maintaining a secure digital environment. Follow these best practices to protect your devices and networks from malware attacks:
- Educate your staff: Teach your team about the dangers of executing attachments and programs from suspicious emails, and the importance of strong, unique passwords.
- Continuously monitor for vulnerabilities: Use automated tools to scan your systems for vulnerabilities and patch them promptly.
- Implement a third-party risk management framework: Ensure your vendors maintain secure systems and follow best practices to minimize the risk of data breaches and leaks.
- Stay informed about emerging cyber threats: Keep up to date with the latest malware trends and share this information with your team.
By following these best practices and staying vigilant, you can minimize the risk of malware infections and protect your valuable data and digital assets.



